Security and compliance
Securing People and Business
Security and functionality are at opposite ends of the spectrum. Creating a high-security network while at the same time limiting the impact on business operations can be complex. We successfully leverage a team of experts collectively possessing the skill and experience to integrate the latest technologies alongside both new existing infrastructures.
We utilize a systematic approach to ensure essential elements like multi-factor authentication are deployed and properly configured. Continuing a progression, we are attentive to the more advanced requirements to protect remote users accessing corporate applications and mobile devices carrying sensitive data.
Success is achieved by formulating a working balance between security and functionality, a balance that concentrates on the interoperation of people and technology.

Protecting What Matters

People
The exploitation of employees is costly. Even basic security awareness training provides significant protection against this type of threat. We offer both self-service and one-on-one awareness training.

Attacks via email are some of the most popular and costly to businesses today. We offer end-to-end security that helps prevent email-born threats that can exploit employees or infect internal networks.

Remote Access
Sleep easy knowing only allowed individuals are accessing corporate applications and data remotely. We create single points of entry, leverage multiple authentication factors, and time limit access, all aimed to prevent unauthorized access.

Laptops and Phones
Is data your data correctly encrypted? We help organizations implement controls to avoid being on the receiving end of damages associated with a data breach linked to lost or stolen laptops and mobile devices.

Audit
We identify all audit all IP aware devices within your organization using advanced software tools

Analysis
We provide an insight into current and potential points of exploitation and create action plans to resolve each

Compliancy
We assist in the improvement of security hygiene and meet industry compliance guidelines
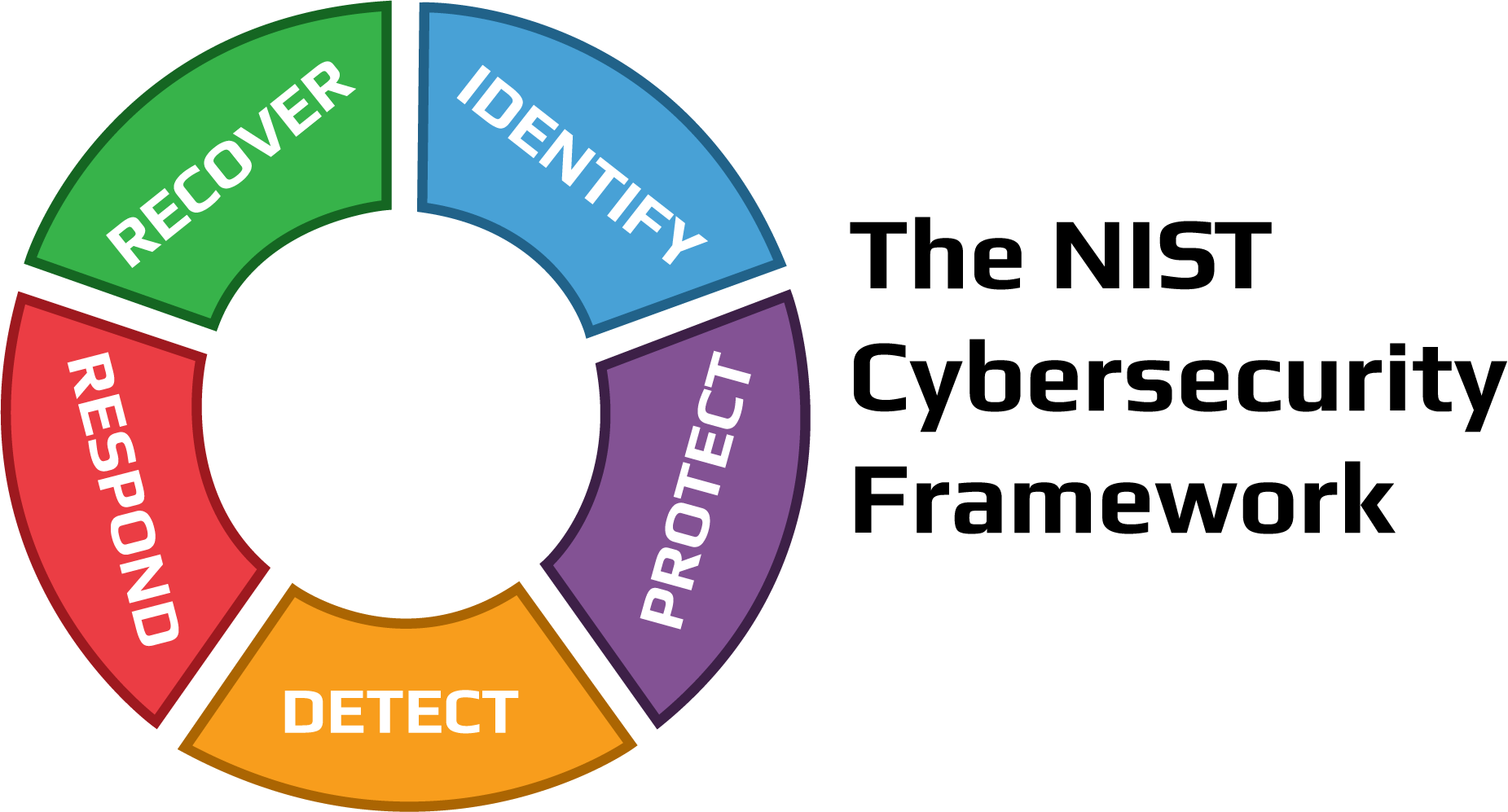
Conform with NIST 800-171 and mitigate risk.
Take a stance on security and protect the data assets of your organization. NIST 800-171 contains 110 controls across 14 control families. While NIST 800-171 focuses on organizations that participate in government contracts, it is a compliancy track that even small organizations can align with on almost any IT budget.
Today’s business world is continually moving toward requiring people and technology to exhibit improved cybersecurity hygiene. Organizations achieving NIST 800-171 compliancy capture more opportunities and put customers and vendors at ease, showcasing a strong posture concerning IT security.
Let our security professionals audit your network and identify possible exposure and risk within your current information technology infrastructure. With over 30 years of low-level network and engineering expertise, we leverage inside knowledge to improve the security of people and businesses.
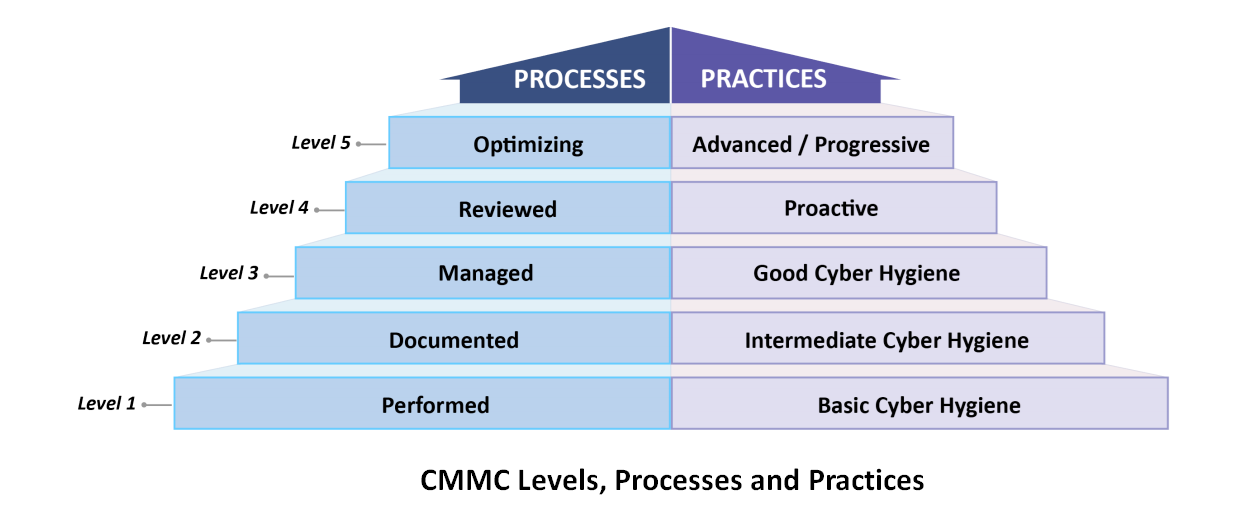
The Purpose of CMMC
CMMC is a government-backed program that establishes a series of compliance levels that help the government assess, whether your business has the security needed to hold and store sensitive data. We prepare your business for CMMC through training and certification and upgrade of hardware. Identify attacks, respond to them, and secure your vulnerable data.
- CMMC is flexible, meaning that there is more than one solution to protect your data.
- As more and more cyberattacks occur every year, it becomes ever more important to establish secure practices and procedures, CMMC outlines the best.

HIPPA Regulations
The viability of a technology brand is more than a flashy logo, being part of a current sales trend, or even a collection of online reviews. Instead, many factors determine technology components and the lasting value they can bring. We know the market and the brands that comprise it. Levering years of field experience integrating and servicing the best and worst offerings, we align our clients with what works and lasts.